Technology
1324hwkeys | Trusted Solution for Secure Key Management

When it comes to key management solutions, security and reliability are non-negotiable. For businesses and professionals managing high-value data, ensuring secure and seamless access to hardware-based authentication is critical. Enter 1324hwkeys, your trusted partner for secure key management.
This post will explore what makes 1324hwkeys the ultimate choice for secure key management, the robust features you can rely on, and why it leads the industry in delivering trusted hardware security solutions.
Why Key Management Matters in Today’s Digital Landscape
With cyber threats escalating globally, businesses and organizations are under constant pressure to protect their sensitive data. Whether it’s managing encryption keys, securing API communications, or safeguarding end-user credentials, reliable key management systems are a must-have.
Failing to use the right tools puts your enterprise at risk of:
- Data breaches and unauthorized access
- Loss of customer trust
- Non-compliance with regulatory standards such as GDPR and HIPAA
- Operational inefficiencies caused by manual or flawed key distribution processes
1324hwkeys eliminates these risks with cutting-edge key management solutions tailored for modern security challenges.
What Sets 1324hwkeys Apart?
There are numerous key management tools available today. However, few can match the robust features, ease of integration, and unwavering reliability offered by 1324hwkeys.
1. State-Of-The-Art Hardware Security Modules (HSMs)
At the core of 1324hwkeys’ solutions are industry-leading Hardware Security Modules designed to keep your cryptographic keys safe. Why HSMs? Because they deliver:
- Tamper-proof storage for encryption keys.
- Hardware-accelerated performance for cryptographic operations.
- Additional protection against physical and digital threats.
Industries such as banking, cybersecurity, and government organizations trust HSMs for their security-critical operations—and 1324hwkeys stands unrivaled in providing world-class HSM-enabled solutions.
2. Integration Simplicity
Security doesn’t need to be complicated. That’s why 1324hwkeys provides seamless integration with existing systems to minimize downtime and ensure a hassle-free onboarding process:
- Compatible with leading enterprise platforms.
- Smooth API integrations to maintain workflow continuity.
- Effortless deployment, whether on-premises or via cloud services.
3. Unmatched Scalability
As your business grows, so do your security needs. 1324hwkeys is designed with scalability in mind. From startups managing their first database to large enterprises handling millions of data exchanges per day, 1324hwkeys ensures your systems remain secure at every stage of growth.
4. Enhanced User Control
Security without control is meaningless. 1324hwkeys gives you full visibility and authority over key access and usage:
- Customized user roles ensure only authorized individuals can generate, access, or distribute encryption keys.
- Real-time activity monitoring minimizes vulnerabilities.
- Audit logs for compliance tracking and incident investigations.
5. Compliance Made Easy
Meeting industry compliance standards can be challenging. But with 1324hwkeys, your organization is equipped to meet and exceed these demands:
- Fully adheres to standards like FIPS 140-2, GDPR, and PCI DSS.
- Detailed reporting for regulatory scrutiny.
- Secured architecture that simplifies audits.
Real Use Cases for the 1324hwkeys Solution
Wondering how 1324hwkeys fits into your industry? Here are some examples of industries that benefit from its trusted solutions:
a. Banking and Financial Services
Banks require impeccable encryption standards to protect online transactions and customer data. 1324hwkeys aids in:
- Encrypting cardholder data for PCI DSS compliance.
- Protecting ATM keys and securing interbank connections.
b. Healthcare
Healthcare providers handle highly sensitive patient records. 1324hwkeys ensures:
- Secure storage of patient data for HIPAA compliance.
- Encrypted communication channels between healthcare devices.
c. eCommerce and Retail
Online retailers protect businesses and customer payment information via:
- Digital certification for secure SSL communications.
- Securing backend systems that handle millions of customer records.
d. Government and Defense
Government agencies depend on hardware-based solutions to:
- Secure classified information.
- Maintain national security by protecting critical infrastructure.
Why Businesses Trust 1324hwkeys
1324hwkeys has become synonymous with trust and excellence in the security industry. Here’s what clients love most about their experience:
- Reliability – Deploy once and enjoy a system designed for 24/7 security.
- Expert Support – Our team of security professionals is ready to assist with implementation, troubleshooting, and scaling.
- Cost-Efficiency – While security breaches cost millions, 1324hwkeys provides an affordable preventive solution that ensures peace of mind.
- Trust – Over 2,000 satisfied companies rely on 1324hwkeys globally to secure their sensitive operations—including leaders in banking and healthcare.
Steps to Get Started with 1324hwkeys
Security doesn’t need to wait. Here’s how you can implement 1324hwkeys into your organization and start enhancing your security measures today:
- Request a Demo – See our solution in action with a personalized demo.
- Consult With an Expert – Our team will guide you toward the best configuration for your needs.
- Deploy in Your Organization – Rapidly integrate with your systems without disrupting operations.
- Secure Your Data – Gain peace of mind knowing your encryption keys are safeguarded by the best technology available.
Invest in Confidence with 1324hwkeys
Enterprise-level security is no longer a luxury—it’s a necessity. With 1324hwkeys, your organization won’t just keep pace with modern security demands; you’ll be leading the charge.
Our cutting-edge solutions ensure total control over your cryptographic assets, enhanced compliance, and peace of mind in the face of evolving cyber threats.
Final Thoughts
Organizations today face increasingly sophisticated threats to their data and systems. Investing in robust security solutions like 1324hwkeys is not just about protecting assets—it’s about building trust, ensuring compliance, and staying ahead of the curve. By prioritizing the security of your cryptographic assets, you empower your organization to operate with confidence in an interconnected world. Choose 1324hwkeys to lead your security strategy and safeguard your future.
Conclusion
Security is no longer an optional consideration for modern organizations; it is a critical foundation for sustainable success. By adopting 1324hwkeys, you are taking proactive steps to fortify your cryptographic infrastructure against today’s most pressing threats. This comprehensive solution not only protects valuable data but also establishes a culture of trust and reliability within your organization. Make the choice to stay prepared, compliant, and ahead of the evolving cybersecurity landscape—make the choice to invest in 1324hwkeys.
FAQs
1. What is 1324hwkeys?
1324hwkeys is an advanced cryptographic solution designed to enhance your organization’s security infrastructure. It offers robust protection for sensitive data through state-of-the-art encryption and seamless integration into existing systems.
2. How does 1324hwkeys ensure data security?
1324hwkeys uses cutting-edge hardware encryption technologies to safeguard your critical assets. It protects against unauthorized access, cyber threats, and potential vulnerabilities by delivering high-performance, tamper-resistant security.
3. Is 1324hwkeys compatible with my current systems?
Yes, 1324hwkeys is designed for flexibility and compatibility with a wide range of existing systems. Its seamless integration ensures minimal disruptions and efficient deployment within your organization’s infrastructure.
4. Who can benefit from using 1324hwkeys?
Organizations of all sizes, across various industries, can benefit from the advanced security measures provided by 1324hwkeys. Whether you manage sensitive customer data, financial records, or proprietary information, 1324hwkeys offers the protection you need.
5. How do I get started with 1324hwkeys?
To begin implementing 1324hwkeys, contact our sales and support team today. We will guide you through the process, ensuring a smooth integration and providing the necessary expertise to secure your environment.

Technology
Is hdhubfu Right for You? An In-Depth Look at Its Features

Are you tired of scrolling through endless lists of streaming services, trying to find the perfect fit for your entertainment needs? If so, hdhubfu might just be what you’re looking for. With an intriguing mix of features and content options, this platform has been making waves in the world of online streaming. But is it truly right for you? In this article, we’ll dive deep into everything hdhubfu has to offer—from its standout features and user experience to pricing plans and customer feedback. Let’s uncover if hdhubfu could become your next favorite streaming service!
What sets hdhubfu apart from other streaming services?
hdhubfu distinguishes itself from the multitude of streaming platforms through its diverse selection and user-centric features. With a focus on niche content, it caters to viewers seeking unique films and series that often fly under the radar.
The platform emphasizes accessibility. Users enjoy seamless navigation across various devices, ensuring an uninterrupted experience whether at home or on the go.
Additionally, hdhubfu boasts advanced recommendation algorithms. These curate personalized suggestions based on viewing habits, making it easier for users to discover new favorites without endless scrolling.
Another standout feature is its community engagement. Subscribers can interact through forums and discussions about their favorite shows, fostering a sense of belonging among fans.
These aspects collectively enhance the overall viewing experience, setting hdhubfu apart from more conventional streaming offerings.
The cost and subscription options
When considering hdhubfu, understanding the cost and subscription options is essential. The service offers various plans tailored to different viewing habits. Whether you’re a casual viewer or a binge-watcher, there’s likely something for you.
Typically, users can choose between monthly and yearly subscriptions. A monthly plan provides flexibility if you’re unsure about committing long-term, while the annual option often comes with savings that make it more appealing.
Discounts may be available during promotional periods, making it even easier to join. Additionally, many users appreciate that hdhubfu does not have hidden fees or complicated add-ons.
Payment methods are generally diverse too; credit cards and popular online payment services are usually accepted. This variety allows subscribers to select what best fits their needs without hassle.
Content available on hdhubfu
hdhubfu offers a vast library of content that caters to various tastes and preferences. Whether you’re into movies, TV shows, or documentaries, there’s something for everyone.
The platform boasts a mix of classic films and the latest releases. You can dive into popular genres like action, romance, thriller, and fantasy. For fans of indie cinema or lesser-known titles, hdhubfu provides hidden gems that are hard to find elsewhere.
TV series lovers will appreciate the extensive collection of both current hits and nostalgic favorites. From binge-worthy dramas to lighthearted comedies, viewers have plenty to explore.
Documentary enthusiasts won’t be disappointed either; hdhubfu features insightful pieces covering everything from nature and history to social issues. With fresh content added regularly, boredom is unlikely with this diverse catalog at your fingertips.
User-friendly interface and navigation
Navigating through hdhubfu is a breeze. The user-friendly interface is designed with simplicity in mind, making it easy for anyone to jump right in.
Upon logging in, you’re greeted with a clean layout. Categories are clearly labeled, ensuring that users can find their favorite shows or movies without hassle.
The search function is intuitive. Type in a title or genre, and relevant options appear almost instantly.
For those who love personalized experiences, hdhubfu offers recommendations based on your viewing history. This feature enhances the overall user experience by introducing content tailored just for you.
Additionally, the platform ensures seamless access across devices—whether it’s your smartphone, tablet, or smart TV. You can switch from one device to another with ease without losing track of what you’re watching.
HD quality streaming and device compatibility
hdhubfu excels in providing HD quality streaming, ensuring that every show and movie is visually stunning. The clarity and detail make for an immersive viewing experience. Whether you’re watching a blockbuster film or binge-watching a series, the high-definition output enhances your enjoyment.
Device compatibility is another strong point of hdhubfu. It works seamlessly across various platforms, including smart TVs, tablets, smartphones, and gaming consoles. This flexibility allows you to watch content wherever you prefer without any hassle.
Moreover, the service supports multiple operating systems. Whether you’re on iOS or Android devices, accessing hdhubfu remains straightforward. You can easily switch from one device to another while maintaining your watching progress.
This adaptability makes it simple for users to enjoy their favorite content anytime and anywhere without sacrificing quality.
Pros and cons of using hdhubfu
Using hdhubfu has its advantages. One major benefit is the extensive library of content that caters to various tastes. Whether you’re into movies, series, or documentaries, there’s something for everyone.
Another plus is the affordability of subscription options compared to other platforms. Many users appreciate getting quality entertainment without breaking the bank.
On the flip side, some may find a few gaps in popular titles. While hdhubfu offers a diverse selection, it doesn’t always have every latest release.
Additionally, streaming quality can vary depending on your internet connection. Users with slower speeds might experience buffering issues at times.
Customer support could use improvement as well; response times are not always quick enough to satisfy urgent queries. Balancing these pros and cons will help potential subscribers make informed choices about using this service effectively.
Customer reviews and experiences
Customer reviews for hdhubfu paint a vivid picture of user satisfaction. Many users appreciate the vast selection of movies and TV shows available. They often mention how it feels like having a cinema in their living rooms.
Some users highlight the streaming quality as a standout feature, noting that they enjoy watching content without interruptions or buffering. This aspect seems to elevate their viewing experience significantly.
However, not all feedback is positive. A few subscribers have pointed out occasional glitches during peak hours. Their expectation for seamless service sometimes falls short.
Despite these hiccups, many customers express loyalty to hdhubfu due to its affordable pricing and diverse library. The balance between cost and variety tends to keep viewers coming back for more enjoyable moments spent on the platform.
Is hdhubfu the right streaming service for you?
Choosing a streaming service can be tricky. With so many options, it’s essential to pinpoint what you really value.
If you’re searching for an extensive library of movies and shows, hdhubfu might meet your needs. Its diverse content spans various genres, ensuring there’s something for everyone in the family.
Are you a tech enthusiast? The HD quality streaming is impressive and works seamlessly across multiple devices. This means you can enjoy your favorite titles whether at home or on the go.
However, consider how often you’ll use it. If binge-watching isn’t your style, there may be better alternatives out there that suit occasional viewing habits more effectively.
Also think about budget constraints. While hdhubfu offers competitive pricing, it’s crucial to weigh its cost against features that matter most to you before making any commitments.
Final Thought
Choosing a streaming service can be daunting. With so many options available, finding the right fit is essential.
hdhubfu offers a unique blend of features tailored for diverse audiences. Its content library caters to various tastes, making it appealing to different viewers.
Consider your viewing habits and preferences before diving in. The platform’s user-friendly interface simplifies navigation, enhancing your overall experience.
Technical aspects like HD quality and device compatibility also play a crucial role in decision-making. These factors ensure that you enjoy seamless entertainment across multiple devices.
Listening to customer reviews adds another layer of insight into hdhubfu’s performance in real-life scenarios. Engaging with community feedback may help shape your perspective on whether this service aligns with your needs.
Take time to weigh all these elements carefully as you explore hdhubfu’s offerings and decide if it resonates with you personally.
Conclusion
When considering whether hdhubfu is the right streaming service for you, it’s essential to weigh all factors. The platform offers a unique blend of content, user-friendly navigation, and high-definition quality that appeals to various viewers. Its subscription options are designed to fit different budgets while providing access to an extensive library of films and series.
However, like any service, it has its pros and cons. Some users rave about the vast selection and seamless experience; others may find limitations in specific genres or content availability. Evaluating customer reviews can provide insight into how well hdhubfu meets expectations.
Before making your decision, reflect on what matters most to you in a streaming service—be it price, content variety, interface design or device compatibility. By aligning your preferences with what hdhubfu offers, you’ll be better positioned to determine if this platform suits your entertainment needs.
Choosing a streaming service should enhance your viewing experience without unnecessary complications or costs. Take the time to explore all aspects of hdhubfu before diving in—it could very well become your go-to source for entertainment.
Technology
doodflix vs. Traditional Streaming Services: What’s the Difference?

Streaming services have revolutionized the way we consume content. Gone are the days of flipping through cable channels or waiting for your favorite show to air at a specific time. Now, with just a few clicks, you can access an entire library of movies and series from the comfort of your couch.
Amidst this streaming explosion, a new player has entered the arena: Doodflix. This platform is gaining attention for its unique offerings and user-friendly approach. But how does it stack up against traditional streaming giants like Netflix and Hulu?
Join us as we dive into what makes Doodflix stand out in this competitive landscape. Whether you’re already familiar with it or hearing about it for the first time, there’s much to explore about this intriguing alternative to mainstream options in today’s digital entertainment world.
What is Doodflix?
Doodflix is an innovative streaming service that has recently entered the entertainment landscape. It aims to offer users a unique viewing experience, blending traditional streaming elements with fresh features.
At its core, Doodflix focuses on user-generated content and niche programming. This allows for a diverse range of shows and films that might not be available on mainstream platforms.
One standout feature is its interactive community aspect. Viewers can engage with creators directly, discuss episodes in real-time, or even contribute their own ideas for future content.
With an easy-to-navigate interface, Doodflix emphasizes personalization. Users can customize their watchlists based on preferences and interests.
The platform also boasts an impressive library filled with indie films and underground series, appealing to those seeking something outside the typical Hollywood fare.
Doodflix and Traditional Streaming Services
Doodflix is emerging as a fresh contender in the streaming landscape, challenging established giants. Unlike traditional services that focus on vast libraries of licensed content, Doodflix prioritizes original programming designed to engage niche audiences.
Traditional streaming platforms typically rely on a mix of blockbuster movies and popular TV shows. They cater to mainstream preferences while also introducing some unique offerings. However, they often come with higher subscription costs and extensive packages that may overwhelm viewers.
Doodflix takes a different approach by streamlining its offerings. It focuses on exclusive series and films tailored for specific interests—often overlooked by larger competitors. This specialization can foster deeper connections with users who seek something beyond the standard fare.
While traditional services aim for broad appeal, Doodflix carves out space for creativity and innovation within the industry. Users might find this refreshing in an era saturated with familiar titles across multiple platforms.
Differences between Doodflix and Traditional Streaming Services
Doodflix stands apart from traditional streaming services in several key ways. First, its content curation is often more niche-focused, appealing to specific audiences rather than the general public. This allows viewers to discover unique shows and films they might not find elsewhere.
Another difference lies in the subscription model. While many platforms require monthly fees, Doodflix offers flexible options that cater to varying budgets. Users can choose plans based on their viewing habits without being tied down.
Moreover, Doodflix emphasizes user-generated content and community-driven recommendations. This creates a more interactive experience compared to the polished offerings of traditional services.
The interface also varies significantly; Doodflix champions simplicity over complexity, making navigation intuitive for all ages. Viewers appreciate a design that prioritizes ease of use while still providing access to diverse genres and styles.
What Can You Watch on Doodflix vs. Traditional Streaming Services?
Doodflix offers a refreshing mix of content that caters to niche audiences. You can find indie films, obscure documentaries, and international series that often escape the mainstream radar. This platform thrives on variety.
Traditional streaming services boast extensive libraries filled with popular movies and shows. They showcase blockbuster hits, original series from major studios, and beloved classics adored by many.
If you’re looking for something off the beaten path, Doodflix is your go-to choice. It’s an excellent option for those who want to explore beyond conventional entertainment boundaries.
Conversely, if you crave familiar titles or trending content, traditional platforms are likely where you’ll get your fill. Both options present unique offerings tailored to different viewer preferences.
User Experience: How Does Doodflix Compare to Traditional Streaming Services?
Doodflix offers a refreshing twist on user experience compared to traditional streaming services. Its interface is designed with simplicity in mind, making navigation seamless and intuitive.
Users can easily browse through content without the clutter often found in other platforms. The search function is streamlined, allowing for quick access to favorite shows and movies.
Personalization plays a significant role as well. Doodflix learns viewer preferences over time, presenting tailored recommendations that feel more relevant than ever before.
Loading times are surprisingly fast, enhancing overall enjoyment. There’s minimal buffering, which means you spend less time waiting and more time watching.
Social features like sharing options add an interactive element that many traditional services lack. This fosters community engagement among users who want to discuss or recommend what they’re watching.
The Future of Streaming Services: Will Doodflix Disrupt the Industry?
The landscape of streaming services is rapidly evolving. Enter Doodflix, a platform that’s gaining attention for its unique offerings.
Many industry experts speculate that Doodflix could disrupt traditional models. Its approach to content curation and user engagement sets it apart from the competition.
Doodflix emphasizes community-driven recommendations, allowing users to discover hidden gems rather than just popular titles. This could shift how viewers choose what to watch.
Moreover, its flexible pricing model appeals to budget-conscious consumers. In an age where subscription fatigue is real, offering alternatives can attract a significant audience.
As more people seek personalized experiences, Doodflix’s focus on niche genres may capture market share from established giants. The question remains: will this new contender lead the charge into a different era of entertainment?
Final Thought
Doodflix emerges as a distinct player in the streaming landscape. Its unique approach to content and user engagement sets it apart from conventional services.
With its emphasis on niche offerings and innovative viewing experiences, Doodflix invites users into a realm that feels fresh and exciting. This platform caters to those who crave something beyond mainstream media.
As more viewers seek alternatives, Doodflix may just be tapping into an underserved market. Its potential impact could reshape expectations around what streaming can truly offer.
The industry is evolving quickly, and platforms like Doodflix are at the forefront of this change. Whether they’ll dominate or coexist alongside traditional giants remains to be seen, but their presence certainly stirs curiosity among audiences seeking variety in their entertainment choices.
Conclusion
The landscape of streaming services is constantly evolving. With the rise of platforms like Doodflix, viewers have more options than ever before. Doodflix stands out with its unique approach and offerings, catering to niche audiences while still competing with traditional giants.
As consumers seek variety and affordability, Doodflix’s model may redefine how we consume media. Its focus on user experience and curated content could inspire traditional services to adapt or innovate further.
Whether you prefer mainstream hits or obscure gems, there are choices available at your fingertips. The battle for viewer attention continues, making it an exciting time in the world of streaming. As technology advances and consumer preferences shift, only time will reveal which platform truly wins out in this competitive arena.
Technology
influencersginewuld: Emerging Trends and Technologies to Watch

In a world where digital landscapes evolve at lightning speed, the concept of influencersginewuld has emerged as a game-changer in marketing. This term encapsulates not just the role of influencers but also the innovative strategies and technologies reshaping how brands connect with their audiences. As consumers become increasingly savvy, traditional advertising methods are losing their luster. Enter influencer marketing—a dynamic approach that leverages personal connections and authentic storytelling to drive engagement.
With social media platforms serving as fertile ground for this evolution, staying ahead of trends in influencer marketing is crucial for brands looking to make an impact. The realm of influencersginewuld promises exciting developments on the horizon—each one more fascinating than the last. Get ready to explore what’s trending, what tech is revolutionizing this space, and why understanding these shifts matters now more than ever.
The Power of Influencer Marketing
Influencer marketing has transformed the way brands connect with their audiences. It harnesses the trust and authenticity that influencers have built over time. This connection is invaluable for businesses seeking to enhance their visibility.
Brands tapping into this power can reach niche markets effectively. Influencers often cater to specific interests, allowing companies to target demographics more precisely.
Engagement rates are typically higher than traditional advertising methods. Audiences respond better when they see recommendations from someone they admire or relate to.
Moreover, influencer campaigns can generate genuine conversations around products or services. This organic buzz fosters community interaction, propelling brand awareness further.
As platforms evolve, so do strategies in influencer marketing. Marketers must adapt continuously to stay relevant and impactful in a crowded digital landscape.
Top Emerging Trends in Influencer Marketing
Influencer marketing is evolving at a rapid pace. Brands are beginning to focus on micro and nano-influencers who boast highly engaged audiences. These influencers often yield higher conversion rates because their followers trust them more.
Another trend gaining momentum is the rise of video content. Platforms like TikTok and Instagram Reels encourage short, engaging clips that resonate with viewers. This format allows brands to showcase products in creative ways.
Additionally, authenticity remains crucial. Consumers crave genuine connections and storytelling from influencers rather than polished advertisements. Brands are now prioritizing partnerships with those whose values align closely with theirs, fostering a sense of community.
Sustainability also plays a significant role in modern influencer campaigns. Audiences appreciate eco-conscious messaging, pushing brands to collaborate with advocates for environmental responsibility.
Live streaming offers an interactive experience, enabling real-time engagement between influencers and their audience while providing immediate feedback on products or services being showcased.
Innovative Technologies Used by influencersginewuld
The landscape of influencersginewuld is rapidly evolving, largely due to innovative technologies shaping how brands and creators connect. Artificial Intelligence (AI) plays a crucial role in analyzing audience preferences and predicting trends. Brands can use AI tools to identify the right influencers who resonate with their target market.
Additionally, augmented reality (AR) is gaining traction within this space. It provides immersive experiences that allow users to engage with products in real-time. Imagine trying on makeup or apparel virtually before making a purchase decision.
Blockchain technology also enters the scene by ensuring transparency in influencer marketing campaigns. Smart contracts facilitate secure transactions between brands and influencers, eliminating doubts about authenticity.
These advancements not only enhance user experience but also foster trust among consumers, revolutionizing traditional marketing approaches into more interactive formats.
The Impact of Social Media Platforms on influenersginewuld
Social media platforms play a pivotal role in shaping the landscape of influencersginewuld. They serve as vital channels where influencers connect with their audiences, creating authentic interactions that drive engagement.
These platforms amplify the reach of content, allowing influencers to showcase their personalities and expertise. With features like stories, reels, and live streams, they can share real-time updates that resonate deeply with followers.
Algorithms also influence visibility. Influencers must continually adapt their strategies to stay relevant in crowded feeds. This constant evolution fosters creativity and innovation within the influencer community.
Moreover, social networks provide valuable analytics tools. These insights help influencers gauge audience preferences and refine their approaches for maximum impact.
As trends shift rapidly on these platforms, staying ahead is crucial for success in influencersginewuld. The interplay between technology and human connection creates endless opportunities for growth and engagement.
Benefits and Challenges of Using influencersginewuld
The rise of influencersginewuld brings a slew of benefits for brands. Authenticity is at the forefront, as these influencers often connect with audiences on a personal level. Their recommendations can lead to increased trust and engagement.
Another advantage lies in niche marketing. Influencers cater to specific demographics, allowing brands to reach targeted audiences effectively. This precision helps optimize marketing budgets and improve conversion rates.
However, challenges exist. The constantly changing landscape of social media means that what works today might not resonate tomorrow. Staying relevant requires ongoing adaptation.
Additionally, measuring ROI can be tricky when working with influencersginewuld. Metrics like impressions or likes may not translate directly into sales, complicating campaign evaluations.
Finding the right influencer for your brand’s values and message is crucial yet challenging. Misalignment can lead to ineffective campaigns and potential backlash from consumers who expect authenticity.
The Future of influenersginewuld and Influencer Marketing Industry
The future of influencersginewuld is poised for transformative growth. As brands increasingly recognize the value of authentic connections, influencer marketing will evolve beyond traditional partnerships.
Micro and nano-influencers are set to gain more traction. Their ability to engage niche audiences fosters trust and loyalty among followers. This trend highlights a shift toward quality over quantity in follower counts.
AI-driven analytics will play a crucial role as well. By harnessing data insights, brands can tailor campaigns with precision, ensuring that they resonate deeply with target demographics.
As social media platforms continue to innovate, new features will emerge specifically designed for influencer collaboration. These tools will streamline processes, allowing creators and brands to connect seamlessly.
Moreover, regulations around sponsorships may become stricter. Transparency will be paramount as consumers demand authenticity from their favorite influencers. The landscape is changing rapidly; staying ahead means adapting quickly to these trends.
Final Thought
As the landscape of influencersginewuld continues to evolve, adaptability remains crucial. Brands and creators must stay ahead of the curve.
Engagement is no longer just about likes or shares; it’s about building genuine connections. Authenticity will resonate more than ever in a saturated market.
The rise of niche markets offers exciting opportunities for specialized influencers. These individuals can create meaningful content that speaks directly to their audience’s interests.
Innovative technologies will drive this transformation further. From AI-driven analytics to augmented reality experiences, the possibilities are endless.
Collaboration will be key as brands and influencers navigate these changes together. A united approach can amplify messages and foster loyalty among consumers who crave authenticity.
Staying informed on emerging trends is vital for anyone involved in influencer marketing today. Embracing change ensures relevance in an industry defined by constant innovation.
Conclusion
Influencersginewuld is reshaping the landscape of marketing and communication. As we navigate these emerging trends and technologies, it’s clear that influencer marketing is not just a trend; it’s becoming an essential strategy for brands looking to engage with their audience meaningfully.
The integration of innovative tools and platforms enhances how influencers connect with consumers, making campaigns more data-driven and effective. Social media continues to play a critical role in this evolution, offering new avenues for engagement that were previously unimaginable.
While there are undeniable benefits to leveraging influencesginewuld, challenges still exist. Brands must tread carefully as they adapt to fast-changing dynamics. Authenticity remains key in building trust between influencers and their followers.
As we look ahead, one thing stands out: the influencer marketing industry will only continue to grow. New technologies will emerge, creating exciting opportunities for both brands and creators alike.
Staying informed on these developments can set you apart in this competitive field. Adaptability will be essential as influencersginewuld evolves further into our digital lives. Embracing these changes could lead your brand toward success today and beyond.
-
Finance Blogs10 months ago
70+ Inspirational Jeff Goins Quotes for Writers
-

 Blogger Earnings11 months ago
Blogger Earnings11 months agoLegit Blogger Earnings: 70 Blog Income Reports from Successful Bloggers
-

 How To11 months ago
How To11 months agoHow to Create a WordPress Blog from Scratch: A Step-by-Step Complete Beginner’s Guide (2025)
-
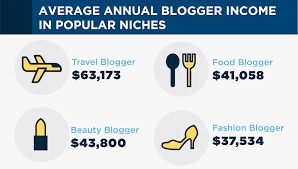
 Blogger Earnings10 months ago
Blogger Earnings10 months agoHow Much Money Can You Realistically Make From Blogging? (Blogger Income Survey Data)
-

 Blogger Earnings10 months ago
Blogger Earnings10 months ago10 Inspiring Crafts Blogs Income and Traffic Reports ($3,000+ monthly)
-
Finance Blogs10 months ago
12 Personal Finance Blogs Income Reports
-

 Finance Blogs10 months ago
Finance Blogs10 months ago40+ Inspirational Ernest Hemingway Quotes for Writers
-

 Finance Blogs10 months ago
Finance Blogs10 months ago40+ Inspiring Neil Gaiman Quotes for Writers